隨著雲計算平台的普及,數據的加密往往在諸多數據處理之前進行,使加密域信號處理的研究受到越來越多的關注。首先從加密和壓縮兩方面同時入手,提出一種針對圖像數據的高安全性加密算法,以及配套的加密圖像壓縮算法。突破加密信號難以壓縮的瓶頸,取得與現有非加密域壓縮方法非常接近的壓縮效率。以構建實際系統的方式,論證了信息論中加密域和非加密域信號壓縮效率可做到近似一致的觀點;此外,針對很多應用場景中不能選擇定制的加密算法,只能使用經典加密算法如RC4或AES的情況,申請人設計一套靈活、高效的可伸縮流密碼加密圖像壓縮系統。在加密域利用基礎層的可壓縮性指導增強層在加密域的編碼。使得用戶可根據帶寬條件和圖像質量需求定制碼流。在壓縮效率和圖像重構質量方面優於現有算法;提出一種高效的加密域可逆信息隱藏算法,摒棄了傳統算法中對額外嵌入密鑰的需求,大幅降低密鑰協商的複雜度。在解碼端,提出一種新型的SVM分類器來區分加密塊和非加密塊。在取得非常高的嵌入量的同時,亦保障原始圖像的近無損恢復;此外,結合安全相似搜索、非局部均值降噪、Yao的混淆電路,構建了加密域的高性能去噪系統,取得了和非加密域非常近似的去噪性能。
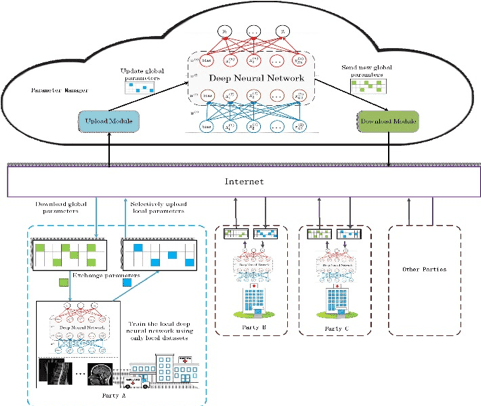
具有隱私保護的深度學習框架
相關文章
[1] J. Duan, J. T. Zhou, and Y. M. Li, “Secure and Verifiable Outsourcing of Large-scale Nonnegative Matrix Factorization (NMF)”, Accepted in IEEE Trans. on Services Computing (T-SC), 2019.
[2] Y. F. Zheng, H. Y. Duan, X. T. Tang, C. Wang, and J. T. Zhou, “Denoising in the Dark: Privacy-Preserving Deep Neural Network Based Image Denoising”, Accepted in IEEE Trans. on Dependable and Secure Computing (T-DSC), 2019.
[3] Y. S. Zhang, J. T. Zhou, Y. Xiang, Y. Zhang, F. Chen, S. N. Pang, and X. F. Liao, “Computation Outsourcing Meets Lossy Channel: Secure Sparse Robustness Decoding Service in Multi-Clouds,” Accepted in IEEE Trans. on Big Data (T-BD), 2018.
[4] Y. M. Li and J. T. Zhou, “Fast and Effective Image Copy-Move Forgery Detection via Hierarchical Feature Point Matching”, IEEE Trans. on Inf. Forensics and Security (T-IFS), vol. 14, no. 5, pp. 1307-1322, 2019.
[5] J. T. Zhou, W. W. Sun, L. Dong, X. M. Liu, O. C. Au, and Y. Y. Tang, “Secure Reversible Image Data Hiding over Encrypted Domain via Key Modulation”, IEEE Trans. on Circuits and Syst. for Video Technology (T-CSVT), vol. 26, no. 3, pp. 441-452, 2016.
[6] J. T. Zhou, O. C. Au, G. T. Zhai, Y. Y. Tang, and X. M. Liu, “Scalable Compression of Stream Cipher Encrypted Images through Context-Adaptive Sampling”, IEEE Trans. on Inf. Forensics and Security (T-IFS), vol. 9, no.11, pp. 1857-1868, 2014.
[7] J. T. Zhou, X. M. Liu, O. C. Au, and Y. Y. Tang, “Designing an Efficient Image Encryption-then-Compression System via Prediction Error Clustering and Random Permutation”, IEEE Trans. on Inf. Forensics and Security (T-IFS), vol. 9, no. 2, pp. 39-50, 2014.




