With the widespread adoption of could computing platforms, data encryption has to be conducted prior to the various data processing tasks. This new trend of data processing makes the research on encrypted-domain signal processing more and more popular. By jointly considering the data encryption and compression, we propose a secure image encryption algorithm, and the accompanied encrypted image compression scheme. The compression efficiency achieved by this encryption-then-compression framework is very close to the one obtained in the plaintext domain, which is a breakthrough of the existing compression paradigms. From the perspective of building up a practical system, our proposed encryption-then-compression framework validates the theoretical finding that encrypted-domain compression can be made equally efficient as the one conducted in the plaintext domain. Furthermore, considering the fact that the encryption algorithms cannot be freely chosen (e.g., only classical RC4 or AES can be adopted) in many practical scenarios, we design a flexible, highly-efficient, scalable compression system for stream-cipher encrypted images. The compressibility obtained in the base layer is treated as a strong side information, which in turn guides the compression in the enhancement layer. Such scalable compression framework enables users to customize the bitstreams according to their bandwidth and quality constraints. The performance in terms of compression efficiency and the quality of the reconstructed images is better than that of the state-of-the-art methods. Furthermore, we suggest a high-capacity image data hiding scheme over encrypted domain, without the need for an additional embedding key, which could significantly save the cost for key exchange and management. At the recipient side, we design a novel and powerful SVM classifier to distinguish encrypted blocks from non-encrypted ones. High-capacity data embedding and near-lossless image reconstruction can be achieved simultaneously. By integrating secure similarity search, non-local mean denoising, and Yao’s garbled circuits, we also build up high-efficiency encrypted-domain image denoising algorithms, which can achieve almost the same performance with the ones for the plaintext domain.
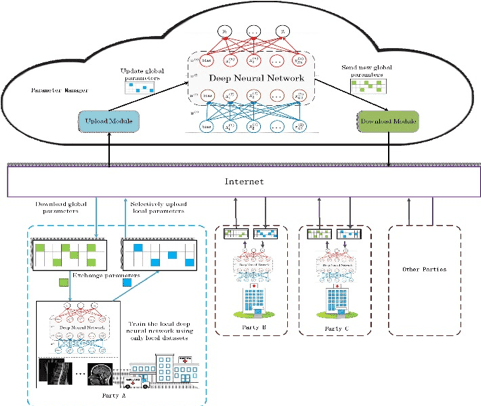
Privacy-preserving deep learning framework
Relevant publication
[1] J. Duan, J. T. Zhou, and Y. M. Li, “Secure and Verifiable Outsourcing of Large-scale Nonnegative Matrix Factorization (NMF)”, Accepted in IEEE Trans. on Services Computing (T-SC), 2019.
[2] Y. F. Zheng, H. Y. Duan, X. T. Tang, C. Wang, and J. T. Zhou, “Denoising in the Dark: Privacy-Preserving Deep Neural Network Based Image Denoising”, Accepted in IEEE Trans. on Dependable and Secure Computing (T-DSC), 2019.
[3] Y. S. Zhang, J. T. Zhou, Y. Xiang, Y. Zhang, F. Chen, S. N. Pang, and X. F. Liao, “Computation Outsourcing Meets Lossy Channel: Secure Sparse Robustness Decoding Service in Multi-Clouds,” Accepted in IEEE Trans. on Big Data (T-BD), 2018.
[4] Y. M. Li and J. T. Zhou, “Fast and Effective Image Copy-Move Forgery Detection via Hierarchical Feature Point Matching”, IEEE Trans. on Inf. Forensics and Security (T-IFS), vol. 14, no. 5, pp. 1307-1322, 2019.
[5] J. T. Zhou, W. W. Sun, L. Dong, X. M. Liu, O. C. Au, and Y. Y. Tang, “Secure Reversible Image Data Hiding over Encrypted Domain via Key Modulation”, IEEE Trans. on Circuits and Syst. for Video Technology (T-CSVT), vol. 26, no. 3, pp. 441-452, 2016.
[6] J. T. Zhou, O. C. Au, G. T. Zhai, Y. Y. Tang, and X. M. Liu, “Scalable Compression of Stream Cipher Encrypted Images through Context-Adaptive Sampling”, IEEE Trans. on Inf. Forensics and Security (T-IFS), vol. 9, no.11, pp. 1857-1868, 2014.
[7] J. T. Zhou, X. M. Liu, O. C. Au, and Y. Y. Tang, “Designing an Efficient Image Encryption-then-Compression System via Prediction Error Clustering and Random Permutation”, IEEE Trans. on Inf. Forensics and Security (T-IFS), vol. 9, no. 2, pp. 39-50, 2014.




